Listen to our podcast 🎧

Introduction
In today’s insurance landscape, every policy, claim, and customer record is a potential target. For CISOs, the biggest risk isn’t always a software vulnerability — it’s the misuse of credentials. Attackers do not need to break systems. They need valid access. That is why credential abuse defense is critical.
Legacy controls like VPNs and weak password policies leave gaps. Once credentials are stolen, attackers can move laterally, escalate privileges, and access sensitive insurance data.
A Zscaler study using Marsh McLennan’s data found 31% of insured cyber incidents could have been prevented with zero trust security architecture.
Insurance CISOs must protect data and reduce cyber-insurance exposure. A robust zero trust strategy for insurance continuously verifies users, devices, and requests. Identity is now the cornerstone of identity-based security in insurance and a key part of any insurance cybersecurity strategy.
So, the question here is how can CISOs prevent credential abuse without slowing operations? What measurable benefits does zero trust provide against breaches? This blog will explore practical steps: implementing zero trust for CISOs, deploying identity threat detection, and aligning security with insurance requirements.

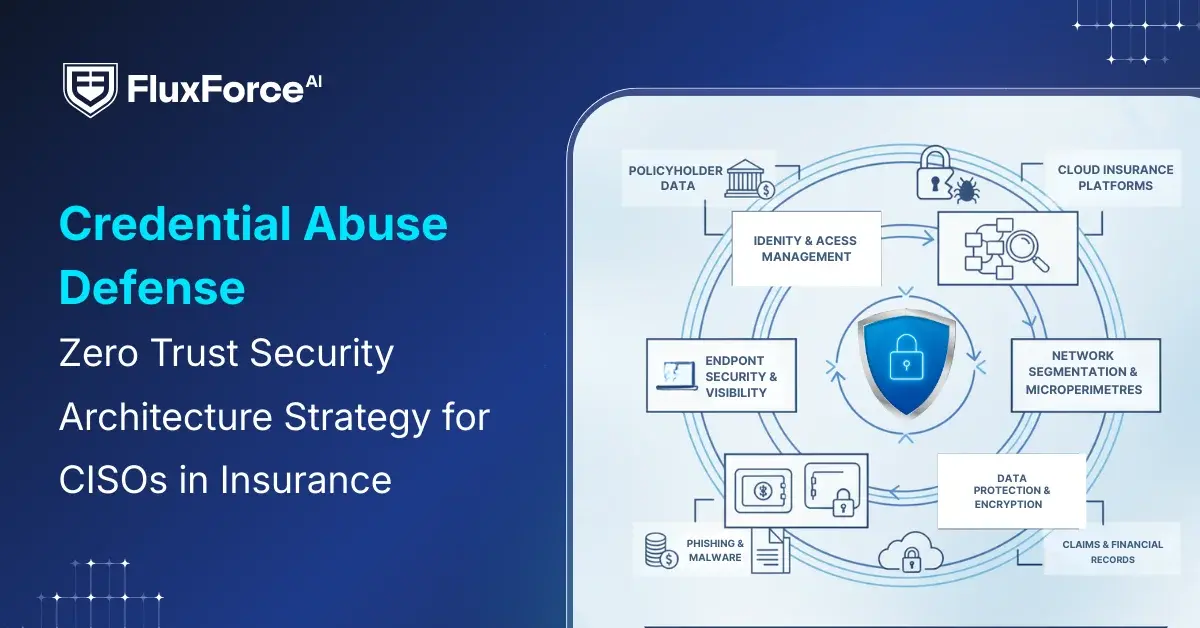
Understanding the threat landscape: What insurance CISOs need to know
Why are credentials the primary attack vector?
Attackers target what gives them the most access with the least effort — valid credentials. In insurance, a single compromised login can expose sensitive client data, claims records, and financial information.
-
Phishing and targeted attacks:
Employees receive emails mimicking clients or vendors. One click can grant full access.
-
Credential stuffing:
Reused passwords from other breaches allow attackers to infiltrate systems easily. Without risk-based authentication, these attacks succeed.
-
Insider misuse:
Disgruntled or negligent employees may exploit privileged access. In insurance, broad access makes this risk critical.
Why traditional defenses fail ?
- 31% of insured cyber incidents could be prevented with a strong zero trust security architecture.
- Average cost of a breach in the insurance sector is $5.97 million
For a CISO, it is about seeing where your gaps are, prioritizing defenses, and protecting customer trust. Next, we explore how a Zero Trust strategy for insurance addresses these challenges directly.
Identity-Centric Zero Trust Strategy for Insurance CISOs
For CISOs in insurance, protecting digital assets goes beyond traditional perimeter security. Credentials have become the primary target, and a single compromised account can expose claims data, customer information, and financial records. A modern Zero Trust strategy for insurance must place identity at the center, ensuring that every access request is continuously verified.

Prioritizing High-Risk Identities
Not all accounts carry the same risk. Executive accounts with access to underwriting or financial data, claims administrators handling sensitive information, and third-party vendor accounts are especially critical. By categorizing and prioritizing these identities, CISOs can focus monitoring, reduce the attack surface, and implement controls where they matter most.
Continuous Identity Verification
A one-time login is no longer sufficient. Continuous authentication, combining multi-factor authentication (MFA) in insurance, device verification, and contextual risk scoring, ensures that unusual access patterns trigger alerts or additional verification. Real-time behavior analysis detects anomalies before attackers can escalate privileges, strengthening overall credential protection in insurance environments.
Enforcing Least Privilege and Just-in-Time Access
Over-permissioned accounts are one of the biggest risks for insurance firms. Enforcing least privilege means employees and vendors only access resources necessary for their roles. Temporary, just-in-time access reduces the window for misuse, while regular audits eliminate stale or outdated permissions. This strategy minimizes the risk of both accidental and malicious data exposure.
Integrating Identity Across Platforms
Insurance operations span cloud services, legacy applications, and third-party systems. A centralized identity and access management (IAM) framework consolidates policies, provides a unified monitoring dashboard, and enables automated remediation when suspicious activity is detected. This integration ensures visibility and control across the entire enterprise, making identity governance proactive rather than reactive.
Identity Threat Detection & Response Strategy for Insurance CISOs
In the insurance sector, stolen credentials often go undetected for days or weeks. Attackers can move laterally, escalate privileges, and access sensitive policyholder data or financial records. For CISOs, this represents a critical operational and regulatory risk. Implementing a robust Identity Threat Detection and Response (ITDR) strategy ensures that suspicious activity is detected promptly and mitigated effectively, reducing both exposure and potential losses.

The Importance of ITDR in Insurance
Traditional controls like VPNs and firewalls cannot detect misuse of valid credentials. ITDR provides continuous visibility across cloud, on-premises, and third-party systems, allowing insurers to spot abnormal behavior before it causes breaches. It is a cornerstone of identity-based security in insurance and strengthens the overall Zero Trust approach.
Monitoring High-Risk Identity Activities
High-risk activities should be prioritized in detection strategies. This includes logins from unusual locations or devices, sudden privilege escalations, and access to large volumes of sensitive data. Integrating ITDR with centralized identity and access management (IAM) platforms allows security teams to correlate events across all systems. This provides a comprehensive view of potential threats and accelerates response times while reducing blind spots.
Automated Response for Rapid Mitigation
Manual intervention is often too slow to prevent breaches. Automated responses allow compromised accounts to be suspended immediately, multi-factor authentication to be enforced, and security teams to receive instant alerts. By automating mitigation steps, CISOs can dramatically reduce attacker dwell time, prevent lateral movement, and contain threats before they impact sensitive insurance operations.
Prioritizing Threats Through Risk Analysis
Not every alert signals a serious incident. CISOs should use contextual risk scoring, historical access patterns, and anomaly detection to identify the most critical threats. High-priority alerts are addressed immediately while low-priority events are logged for review. This approach optimizes resource allocation and ensures that security teams focus on activity most likely to represent credential abuse.
Strategic Integration of Tokenization into Secure Payment Gateways
Integrating tokenization into payment gateways requires careful planning to align with compliance goals and transaction workflows. The following approaches help banks implement tokenization effectively while maintaining PCI-DSS requirements across all payment channels.
1. API-Level Integration for Real-Time Payments
Banks integrate tokenization at the API layer so that PANs are replaced with tokens before entering core systems. This strengthens gateway security for online, mobile, and in-app transactions where interception risks are higher.
2. Multi-Domain Tokenization Across Payment Channels
Multi-domain tokenization assigns channel-specific tokens for ATM, POS, and digital payments. It limits cross-channel exposure and provides clear visibility into token usage patterns across different banking systems.
3. Integration with Fraud Management Systems
Tokens are linked with fraud detection and risk scoring systems, allowing banks to analyse transactions without exposing sensitive cardholder data, ensuring payment security while maintaining PCI-DSS compliance.
Mitigating Compliance and Security Risks
Tokenization reduces many compliance challenges, but banks must still implement clear controls to prevent gaps. Consistent oversight ensures that tokens behave as intended across distributed systems and multi-vendor environments. Compliance Directors can mitigate risks through the following measures:
- Regular validation of tokenization controls to ensure tokens are generated, stored, and used according to PCI-DSS guidelines.
- Monitoring token vault access logs for unusual activity, failed requests, or unauthorized retrieval attempts.
- Ensuring alignment with PCI-DSS Level 1 requirements across all teams handling payment data workflows.
- Conducting periodic mapping reviews to confirm accurate linkage between tokens and original PANs in settlement and dispute processes.
Industry-specific insights and Implementations Best Practices
Tokenization practices vary across banking environments due to differences in transaction volume, regulatory expectations, and infrastructure maturity. Compliance Directors overseeing implementation can improve outcomes by following industry-aligned best practices.

1. Aligning Tokenization with Banking Compliance Models
Banks achieve stronger PCI-DSS compliance when tokenization is embedded into existing risk governance frameworks. This ensures consistent application across new digital banking projects, vendor integrations, and payment modernization initiatives.
2. Using Fintech Tokenization Tools for Rapid Deployment
Fintech-led tokenization platforms support faster integration for banks adopting new digital payment systems. They offer pre-built APIs, cloud-native vaults, and compliance automation, helping banks accelerate PCI-DSS alignment.
3. Ensuring Resilience in Cross-Border and Multi-Currency Transactions
Banks processing international payments use tokenization models that support multi-currency routing and regional data privacy regulations. This strengthens compliance for cross-border transactions without adding operational overhead.
4. Coordinating Tokenization with Data Masking and Encryption
Tokenization works best when paired with masking for logs and encryption for storage. Coordinated controls ensure cardholder data remains protected across all environments not covered by the tokenization model.
Risk Quantification & Cyber-Insurance Alignment for Insurance CISOs
For insurance CISOs, cyber risk is measurable and directly linked to financial impact, regulatory compliance, and customer trust. Credential compromise remains the most significant threat, affecting claims systems, underwriting processes, and sensitive policyholder data. Quantifying these risks and aligning them with cyber-insurance obligations ensures that security investments are actionable.
Identifying and Measuring High-Value Risks
Executive accounts, claims administrators, and third-party vendor logins often control access to the most sensitive data. CISOs must evaluate the potential consequences if these identities are compromised. This includes breach remediation costs, regulatory fines, reputational damage, and operational disruption. Assigning measurable risk scores to each account enables credential abuse defense to focus on the highest-impact areas.
Prioritizing Threat Mitigation Based on Risk
Data from identity and access management (IAM) and ITDR tools should guide decision-making. CISOs can track failed MFA attempts, unusual login locations, and anomalies in access patterns to determine where threats are most urgent. This risk-based prioritization allows security teams to allocate resources efficiently and implement targeted controls without slowing critical insurance operations.
Aligning Security Controls with Cyber-Insurance
Insurance policies increasingly require proof of proactive identity protection and continuous monitoring. A mature Zero Trust strategy for insurance demonstrates:
- Continuous identity verification and contextual access evaluation
- Enforcement of least privilege and just-in-time access
- Automated detection and response to credential abuse
- Comprehensive reporting aligned with regulatory and insurer requirements
By documenting these controls and showing measurable risk reduction, CISOs strengthen relationships with insurers, improve underwriting outcomes, and ensure faster response times for incident claims.

Conclusion
For insurance CISOs, the stakes are high because one stolen credential can expose sensitive claims and financial information. Credential abuse is a constant threat, but the right approach turns it from a worry into a manageable challenge. By knowing which accounts matter most, monitoring them closely, and having automated responses ready, CISOs can stop incidents before they escalate. Combining this with a clear picture of risk and insurance alignment ensures that security decisions are measured, practical, and directly tied to protecting both data and the business.






Share this article