Listen to our podcast 🎧

Introduction
Vendor partnerships are accelerating across organizations to improve business performance. Most enterprises now work with anywhere from 200 to 12,000 suppliers, based on operational scale.
While varied suppliers support savings and speed within the supply chain, broader access across interconnected networks also elevates cyber exposure. Weak third-party security posture has already caused organizations millions in losses — slowing procurement, disrupting production, and affecting delivery performance.
Even with strong controls in place, constant changes across the supplier network make some risks harder to see early. Chief Procurement Officers are now focusing on smarter ways to measure how secure each partner truly is.
Vendor Cyber Posture Ratings provide Chief Procurement Officers a clear and continuous view of security maturity across the supply chain, helping reduce risk and keep operations moving without interruption.
Why vendor cyber posture ratings are becoming standard practice ?
Over 60% of supply chain cyber incidents originate from third-party exposure. With supplier networks expanding, real-time vendor vulnerability insights are essential. Adopting cyber posture ratings helps CPOs avoid blind sourcing risks.
- Supplier attack surface expansion- Cloud migrations, remote access, and SaaS partnerships create new paths for lateral breaches. A single misconfiguration or exposed credential in a vendor environment becomes a gateway into the enterprise network.
- Rising regulatory accountability for third-party failures- CPOs are now directly accountable under mandates such as NIS2, DORA, PCI-DSS, and industry-specific compliance laws. Ratings prove due diligence—before an incident becomes a headline.
- Increased targeting of lower-tier suppliers- Attackers exploit the least-secured entity in the chain. Tier-3 and Tier-4 vendors rarely have robust controls but can access critical systems through integration bridges.
How CPOs across organizations assess vendor cyber posture ?
CPOs combine security cleanliness scores with continuous posture monitoring to understand not only how secure a vendor is today, but how their maturity evolves throughout engagement. Here are practical steps procurement functions adopt before awarding a contract:
1. Checking supplier threat exposure
CPOs review exposed digital assets, leaked credentials, and vulnerabilities visible across the open internet. This helps identify suppliers facing active exploitation risks based on their attack surface and threat signals linked to operational access points.
2. Evaluating security hygiene and control strength
Assessment focuses on practical control performance, including MFA adoption, privileged access security, data encryption, and detection capabilities. The overall cyber cleanliness helps forecast the likelihood of intrusion during operational collaboration.
3. Comparing security levels with similar vendors
Procurement leaders compare supplier ratings with similar vendor categories and contract criticality to ensure cyber maturity aligns with business risk. A below-benchmark posture highlights suppliers needing improvement before onboarding.
4. Setting security rules in contracts
Cyber posture metrics guide the inclusion of SLAs, compliance obligations, and remediation timelines during contracting. This ensures vendor performance is continuously governed through enforceable commitments aligned to procurement risk tolerance.
5. Auditing high-risk suppliers more often
Procurement teams use cyber posture intelligence to determine which suppliers require deeper verification or corrective assessments. Vendors supporting critical operations or showing high threat exposure receive focused evaluation to maintain supply chain stability.
Key Strategies to Prevent Supply Chain Cyber Attacks
Ensuring security in supplier networks is not handled by one team alone. A comprehensive shared responsibility across departments helps achieve better oversight and prevent avoidable vendor-related disruptions. Below are some effective actions:
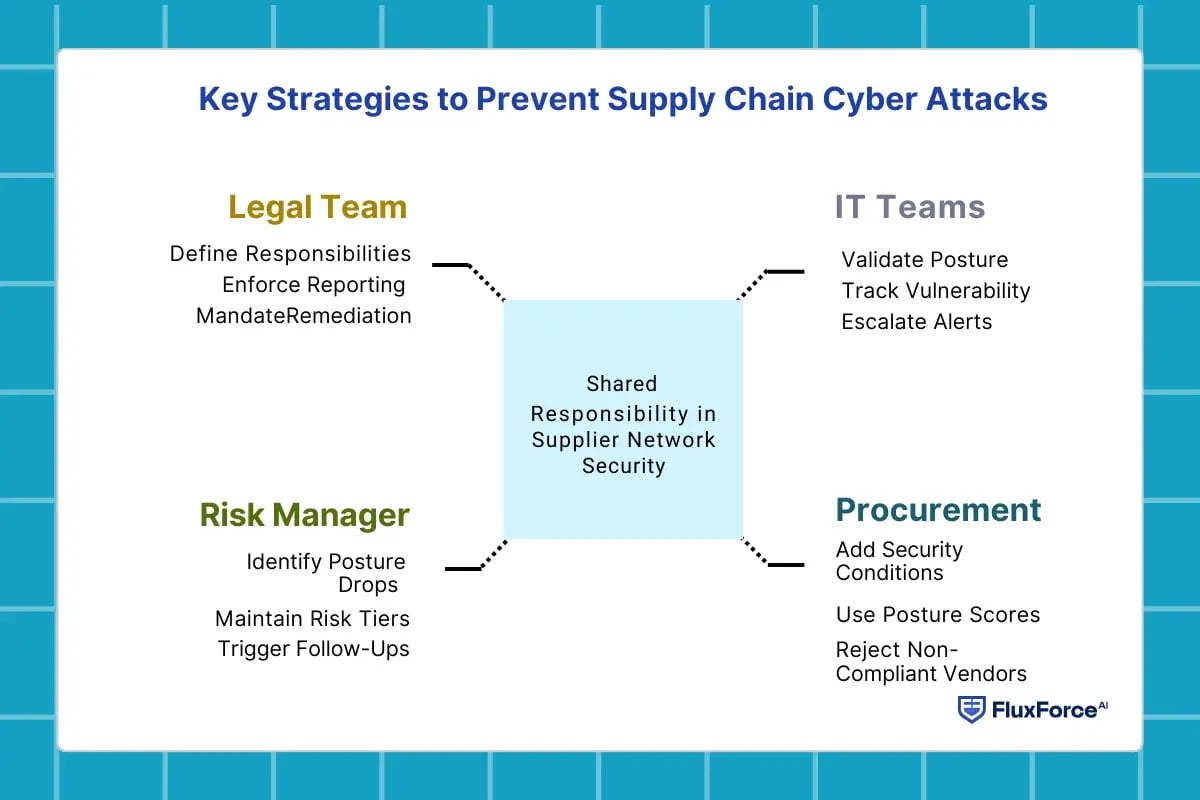
For IT teams- Checking vendor’s cyber rating
- Validate posture before approvals
- Track shifts in vulnerability exposure
- Escalate alerts for critical suppliers
For Procurement- Including security as a requirement
- Add cybersecurity conditions in Request for Proposal (RFPs)
- Use posture scores for faster sourcing
- Reject vendors failing hygiene criteria
For Risk Manager- Continuous monitoring
- Identify posture drops in real time
- Maintain risk tiers across vendors
- Trigger follow-ups on high-severity findings
For Legal team- Adding rules in contract
- Define cyber responsibilities and audits
- Enforce breach reporting timelines
- Mandate remediation in a fixed period
Outcomes of Data-Driven Vendor Cyber Ratings for Procurement
Data-driven vendor cyber ratings provide procurement teams with measurable insights into supplier risk. By combining continuous monitoring with scoring, CPOs can make faster, evidence-based sourcing decisions, prevent operational disruptions, and maintain compliance across the supply chain.
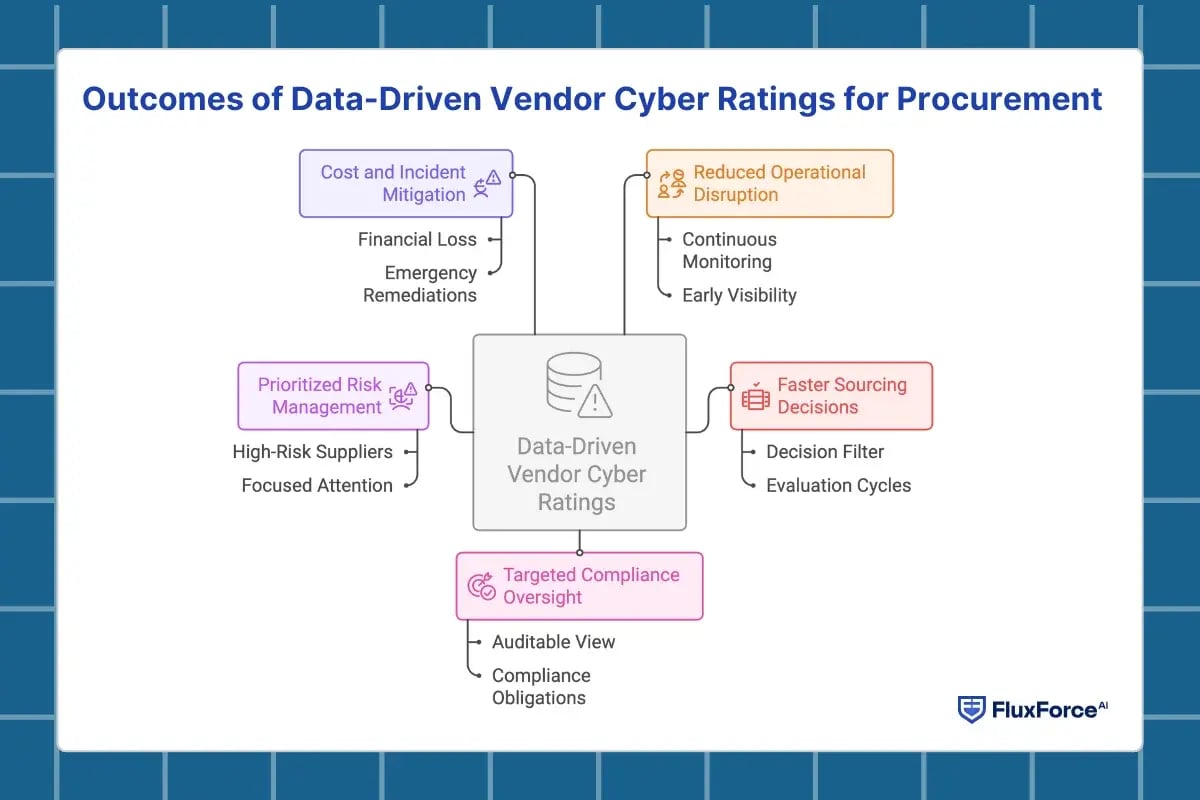
Key benefits include:
- Reduced Operational Disruption- Continuous ratings highlight vendors with weak security, allowing procurement to avoid partners likely to cause production or delivery delays. Early visibility ensures smoother operations and fewer unexpected interruptions.
- Faster, Evidence-Based Sourcing Decisions- Cyber ratings act as a decision filter, helping teams prioritize vendors with stronger posture while identifying high-risk partners for further review. This reduces evaluation cycles without compromising security.
- Targeted Compliance Oversight- Ratings provide a clear, auditable view of vendor security performance. Procurement teams can focus audits and reporting on suppliers that pose regulatory or contractual risk, ensuring compliance obligations are consistently met.
- Prioritized Risk Management- By highlighting high-risk suppliers, procurement can allocate monitoring and remediation resources more efficiently. Critical vendors or those with evolving risk profiles receive focused attention to prevent downstream issues.
- Cost and Incident Mitigation- Data-driven insights help avoid financial loss due to breaches or operational failures. Procurement can proactively reduce costs associated with emergency remediations, downtime, or supplier replacement.
Best practices for vendor cybersecurity evaluation

1. Implement continuous vendor security scoring
Use ongoing assessments to track vendor security posture over time. Continuous scoring identifies emerging risks, supports evidence-based decisions, and allows procurement to prioritize vendors that meet or exceed the organization’s cyber risk standards.
2. Enforce governance and cyber compliance
Integrate security requirements directly into procurement policies and contracts. Clear rules, periodic audits, and compliance checks ensure suppliers maintain controls, regulatory alignment, and accountability throughout the engagement lifecycle.
3. Automate risk monitoring and reporting
Leverage AI-enabled dashboards and alerts to track changes in vendor posture in real time. Automation reduces manual oversight, ensures timely responses to emerging threats, and allows procurement teams to focus on strategic risk decisions.
4. Align vendor evaluation with strategic risk priorities
Tailor cybersecurity assessments to operational criticality and supplier risk tiers. By focusing on high-impact vendors, procurement can allocate resources efficiently, mitigate the most significant exposures, and reinforce supply chain resilience.
Integrating FluxForce AI for Automated Vendor Security Intelligence
FluxForce provides high-risk supply chain organizations with a ready-to-integrate AI solution that continuously monitors vendor security, analyses posture changes in real time, and generates actionable insights. For procurement teams, it saves hours of time and helps make faster decisions while securing supply chains at an enterprise level.
Key Capabilities of Our AI Modules
- Automated Dashboards- Central dashboards track vendor risk levels and security trends, allowing procurement to identify high-risk suppliers and respond quickly to potential threats.
- Predictive Cyber Posture Reports- AI forecasts vulnerabilities based on historical and real-time data, helping teams anticipate risks and take proactive mitigation actions.
- Continuous Threat Alerts- Alerts notify procurement of sudden posture changes or emerging vulnerabilities, reducing exposure and enabling timely interventions.

Conclusion
Vendor cyber posture ratings are more than numbers; they reveal how secure each supplier truly is. For CPOs, this clarity makes decisions easier, from choosing the right vendors to managing risk across the supply chain. Continuous monitoring and clear contract requirements mean fewer surprises, smoother operations, and stronger relationships with trusted partners.
When procurement teams focus on real insights instead of static checklists, the entire supply chain becomes more resilient. Ultimately, these ratings help CPOs balance speed, cost, and security—turning cyber intelligence into a practical tool that supports smarter, safer, and more confident sourcing decisions.






Share this article