Listen to our podcast 🎧
%20(1).jpeg)
Introduction
Banking payment security is no longer effective with “once inside, trusted forever” defence models. With institutions expanding from traditional branches to online platforms, fintech ecosystems, and open banking networks, the risks of cyber frauds are escalating.
Legacy perimeter-based models leave financial systems exposed. Hackers who gain initial access can move freely, steal sensitive data, and initiate fraudulent transactions without detection.
To counter this, zero trust–driven fraud prevention is reshaping how financial institutions protect payment environments. It applies modern risk-based checks with continuous authentication to ensure banks reduce vulnerabilities.
In this blog, we will explore how Zero Trust access control strengthens banking compliance, improves payment security, and equips risk officers with practical strategies to combat evolving threats.
Zero Trust Access Control for Stronger Banking Compliance and Payments Security
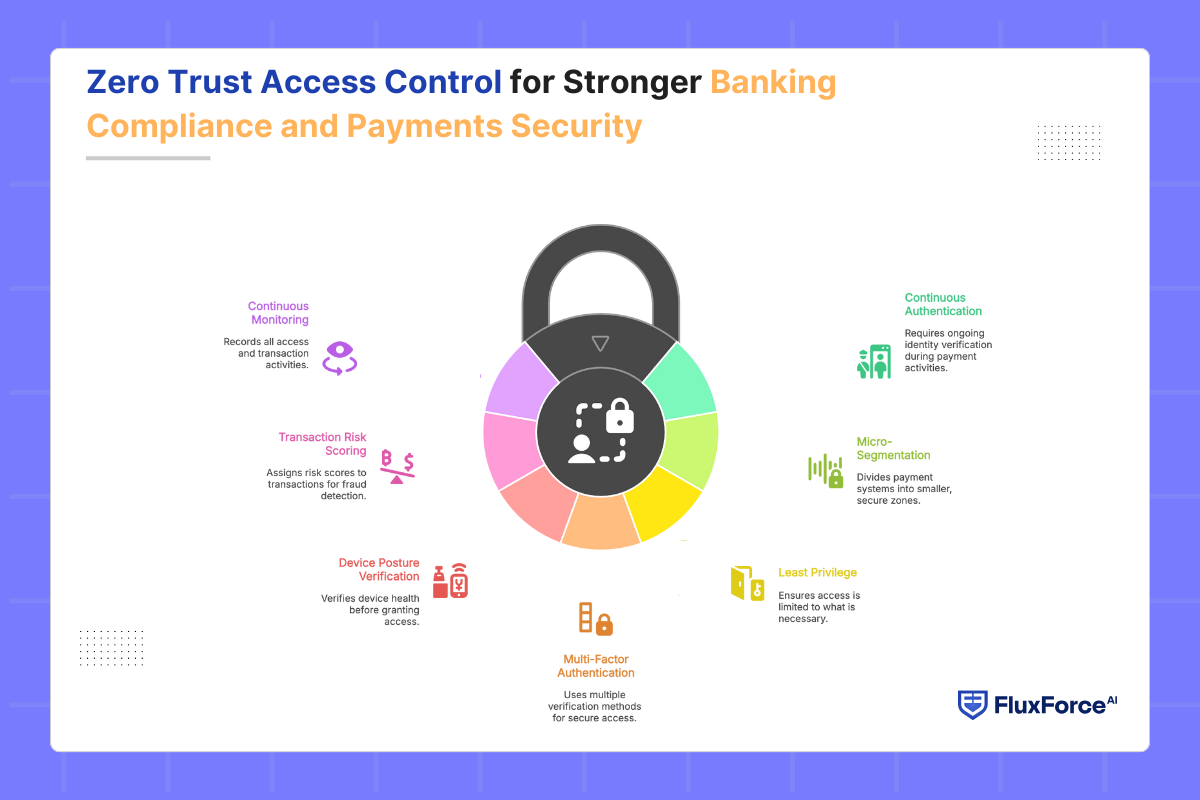
Banking payment security demands robust protection against cybercrimes and insider threats. Zero Trust access control replaces legacy “trusted once inside” defences with assume breach banking approach.
For payment risk officers, Zero Trust offers a structured way to reduce payment fraud and ensure regulatory compliance. Its core workings include:
- Continuous Authentication Throughout Login Sessions- Instead of one-time login checks, Zero Trust requires identity verification throughout payment activities. This limits the risk of account takeover fraud and reassures regulators stronger authentication.
- Micro-Segmentation Across Networks- Zero Trust divides payment systems into smaller security zones. It restricts attackers from moving freely and keeps transaction data compliant with data protection regulations.
- Least Privilege for Minimal Access Rights- Zero Trust policy ensures employees and partners only access what they truly need. This restricts insider fraud, controls vendor exposure, and demonstrates compliance with regulatory principles.
- Multi-Factor Authentication for Secure Payment Access MFA enhances payment login and transaction security beyond passwords. It verifies identity with OTP or biometrics to reduce credential theft risks and ensure compliance.
- Device Posture Verification for Secure Access- Zero Trust verifies device health every time before providing access. It checks encryption, patches, and compliance policies to prevent insecure endpoints from connecting with payment systems.
- Transaction Risk Scoring for Fraud Detection- Under this architecture, every transaction receives a dynamic risk score. Suspicious activities trigger adaptive responses, enabling fraud prevention while meeting regulatory expectations.
- Continuous Monitoring for Regulatory Reporting- Zero Trust records all access and transaction activities. This ensures real-time oversight, simplifies audit readiness, and demonstrates adherence to financial compliance standards.
Key Banking Access Control Strategies for Payments Risk Officers
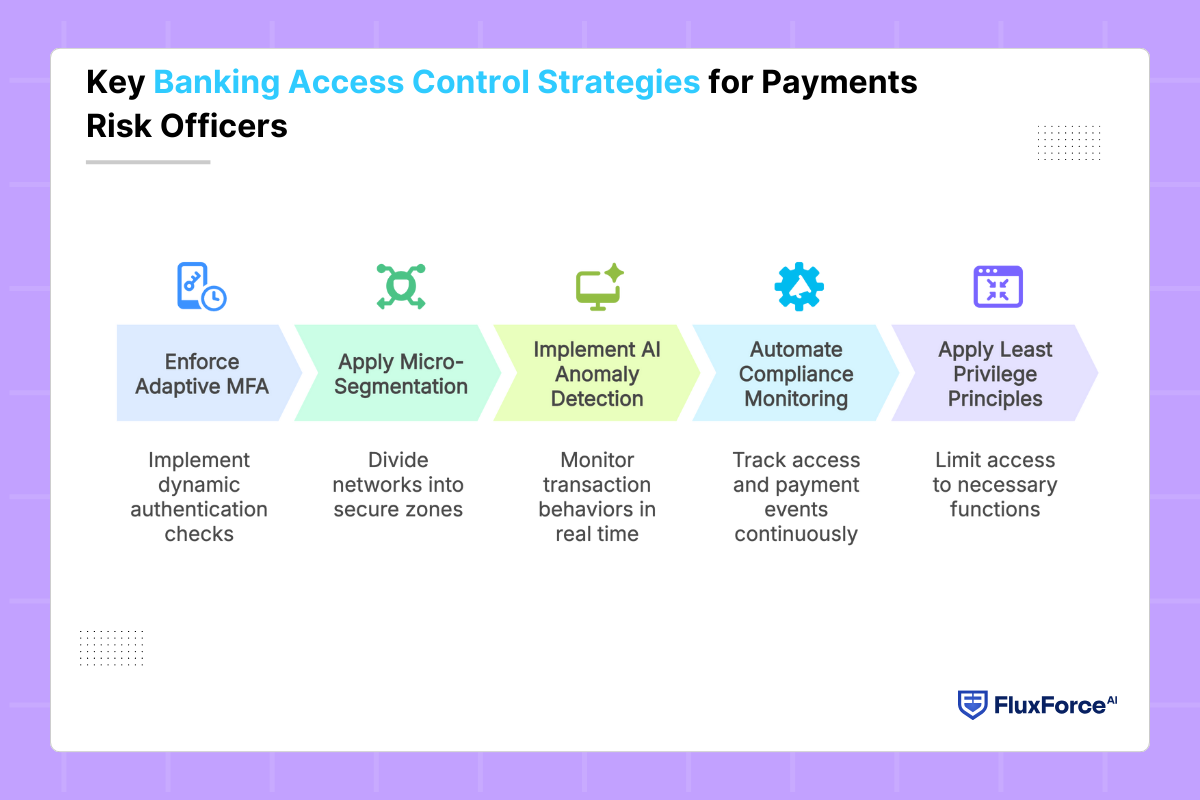
Banks spend millions yearly on fraud detection yet still face breaches. The issue lies not in spending but in applying strategic access controls. Here are five approaches risk officers must prioritize.
- Enforce Adaptive Multi-Factor Authentication Across Payments
Adaptive MFA adds dynamic checks based on transaction context. It strengthens identity assurance, reduces credential theft risks, and aligns with PCI DSS requirements for layered payment authentication security.
- Apply Micro-Segmentation to Restrict Unauthorized Movement
Micro-segmentation divides networks into secure zones. By limiting lateral movement, it prevents attackers from reaching sensitive payment systems, protecting critical assets from breaches and compliance violations.
- Implement AI-Driven Anomaly Detection for Fraud Prevention
AI monitors transaction behaviours in real time. It flags unusual access or payment activity, enabling faster responses and ensuring fraud detection remains proactive and regulatory compliant.
- Automate Compliance Monitoring and Reporting Processes
Automation tracks access and payment events continuously. It simplifies regulatory reporting, reduces manual oversight errors, and ensures payment environments remain aligned with evolving compliance requirements.
- Apply Least Privilege Principles for Access Governance
Access is limited strictly to necessary functions. By removing excessive user rights, banks minimize insider threats, reduce fraud exposure, and strengthen governance for sensitive payment operations.
-1.png?width=1200&height=628&name=hubspot%20blog%20(6)-1.png)
Shaping the Future of AI in Finance
Fluxforce research uncovers how banks and enterprises are adapting to fraud, compliance, and data challenges in 2025.
Benefits of Zero Trust Security Architecture for Banking Payments
Zero Trust modernizes banking payment security by addressing the weaknesses of perimeter-based models. Its benefits include:
- Enhanced Fraud Prevention and Transaction Security: Zero Trust verifies every identity, device, and transaction request in real time, applying continuous authentication and contextual scoring to stop fraud before execution.
- Stronger Compliance and Audit Readiness: With granular access policies and automated reporting, Zero Trust aligns banking operations with evolving regulations and simplifies complex audit requirements.
- Improved Operational Resilience: Micro-segmentation and least-privilege principles isolate intrusions instantly. Even if attackers gain entry, critical payment systems remain protected.
- Enhanced Customer Trust: Customers experience secure, seamless payments. Reduced fraud incidents and transparent protections foster lasting confidence in digital banking platforms and financial services.
Implementing Zero Trust for APIs and Third-Party Payment Integrations
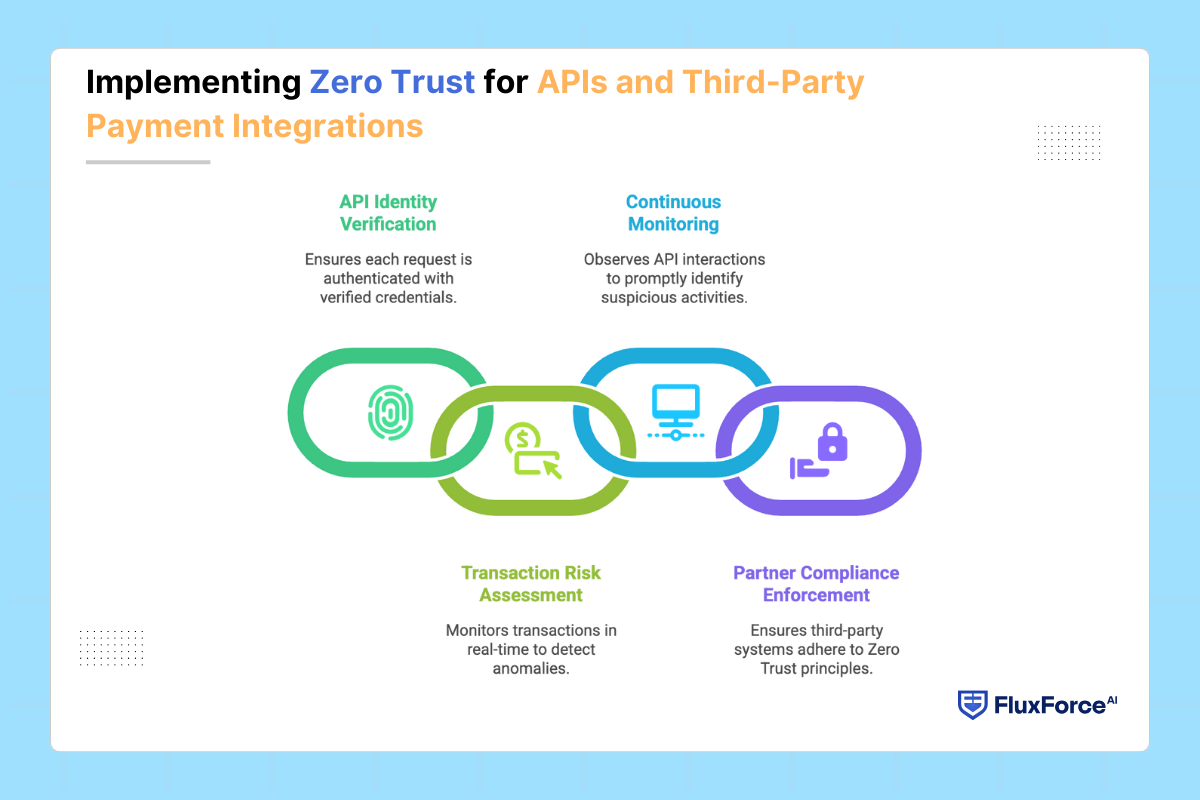
Digital banking and fintech partnerships rely significantly on APIs to process payments and share financial data. Each integration is a potential entry point for fraud or unauthorized access.
In 2023, almost 89% of financial services organizations reported attacks on their APIs, showing how common these risks have become. Zero Trust architecture addresses these challenges by ensuring that every request, transaction, and device is continuously verified before granting access.
Key Implementation Measures:
- API Identity Verification: Authenticate each request using verified credentials and device checks.
- Transaction Risk Assessment: Monitor transactions in real time to detect unusual patterns.
- Continuous Monitoring: Observe API interactions continuously to identify and respond to suspicious activities promptly.
- Partner Compliance Enforcement: Ensure that third-party systems adhere to the same Zero Trust principles, maintaining consistent security across the ecosystem.
Operational Best Practices in Zero Trust Payments Security
Zero Trust in payments ensures every user, device, and transaction is verified. Implementing it requires a clear strategy, combining multiple controls, continuous monitoring, and compliance oversight to reduce fraud without disrupting legitimate payments.
- Staged Implementation for Strategic Control
Roll out Zero Trust controls incrementally, starting with identity verification and MFA. Gradual deployment allows teams to adapt, validates processes, and reduces disruption to payment operations.
- Adaptive Multi-Factor Authentication
Use continuous authentication that adjusts to device posture, behaviour, and location. Adaptive MFA strengthens fraud prevention while ensuring legitimate payment transactions remain smooth and unobstructed.
- Leveraging Pre-Built Zero Trust Frameworks
Implement trusted vendor models to reduce configuration errors, accelerate compliance, and maintain uninterrupted payment flows during security enhancements.
- Real-Time Transaction Risk Scoring
Evaluate transactions dynamically based on size, frequency, and device trust. Suspicious activity is blocked immediately, while valid payments proceed without friction.
- Ethical Monitoring and Compliance Alignment
Combine continuous monitoring with ethical data handling and regulatory adherence. This approach preserves customer trust, ensures compliance, and strengthens overall payment ecosystem security.
Conclusion
Banks handling digital payments and fintech partnerships face rising fraud risks and strict regulatory pressures. Traditional access controls leave sensitive systems exposed.
Zero Trust security provides a practical solution by verifying every user, device, and transaction continuously. Applying strategies like phased implementation, adaptive authentication, transaction risk scoring, and ethical monitoring ensures robust protection without disrupting operations.
Pre-built Zero Trust frameworks built by FluxForce offers plug-and-play models for banks managing high transaction volumes while meeting regulatory requirements.
For payments risk officers, these simple models create a secure, compliant, and resilient environment for reducing fraud, safeguarding data, and sustaining customer trust in complex banking ecosystems.


-1.webp)
.webp)


Share this article