Listen to our podcast 🎧
%20(1)-1.png)
Introduction
In banking, defining access control is a fundamental process for protecting the institution’s most sensitive assets. For years, banks relied on perimeter-based models that granted broad data access once inside the system.
With rising attack sophistication, this approach shows clear weaknesses. In 2024, the average cost of a data breach in banking reached $6.08 million—about 22% higher than the global industry average. This brings the need for robust security policies.
Zero Trust Security Architecture (ZTA) has emerged as the strategic framework to meet this demand. Unlike perimeter-based models, Zero Trust follows the principle of “never trust, always verify,” redefining access controls and reinforcing customer trust.
This blog explores how banking operations leaders can strengthen access controls with Zero Trust and implement it as a forward-looking security strategy.
Common Financial Services Security Gaps
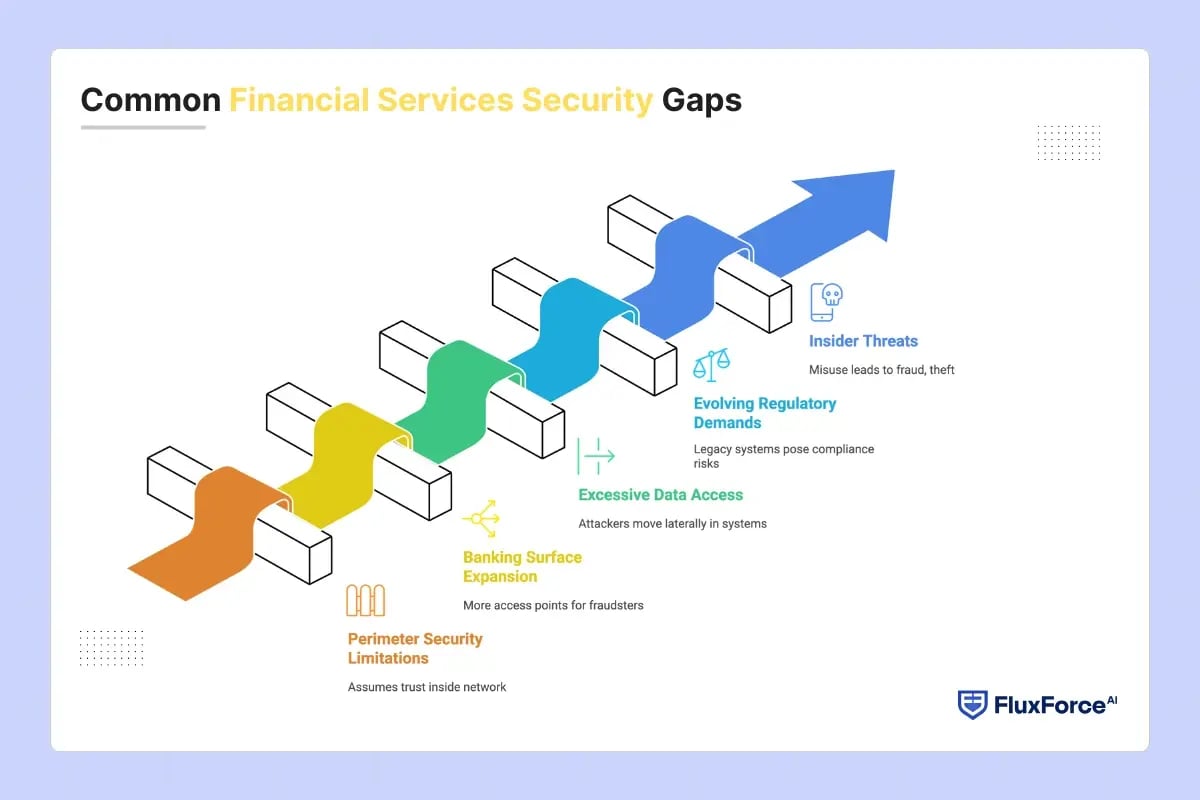
Despite significant investments in cybersecurity, many banks still rely on outdated access controls and fragmented security practices. These gaps leave institutions vulnerable to fraud, regulatory penalties, and reputational damage. Key factors contributing to these vulnerabilities include:
- Perimeter-Based Security Limitations- Traditional perimeter defences assume users are trustworthy once inside the network. With cloud platforms, mobile apps, and APIs, this model poses significant security challenges.
- Banking Surface Expansion- Open banking initiatives, fintech integrations, and third-party APIs increase the number of access points for fraudsters. A single compromised account infiltrates multiple layers of core systems.
- Excessive Data Access- Weak access governance allows attackers or compromised accounts to move laterally within systems. They reach core banking applications and bypass segregation-of-duties policies.
- Evolving Regulatory Demands- Regulators now demand real-time monitoring, continuous access validation, and detailed audit trails. Legacy security systems fail to deliver these capabilities and pose non-compliance risks.
- Insider Threats- Employees and contractors hold broad access to sensitive information. Misuse of accounts, whether intentional or accidental, leads to fraud, theft, and operational interruptions.
These security gaps demonstrate that traditional models are no longer sufficient and highlight the need for robust security frameworks such as Zero Trust policies.
Implementing Zero Trust Policy for Financial Services Security
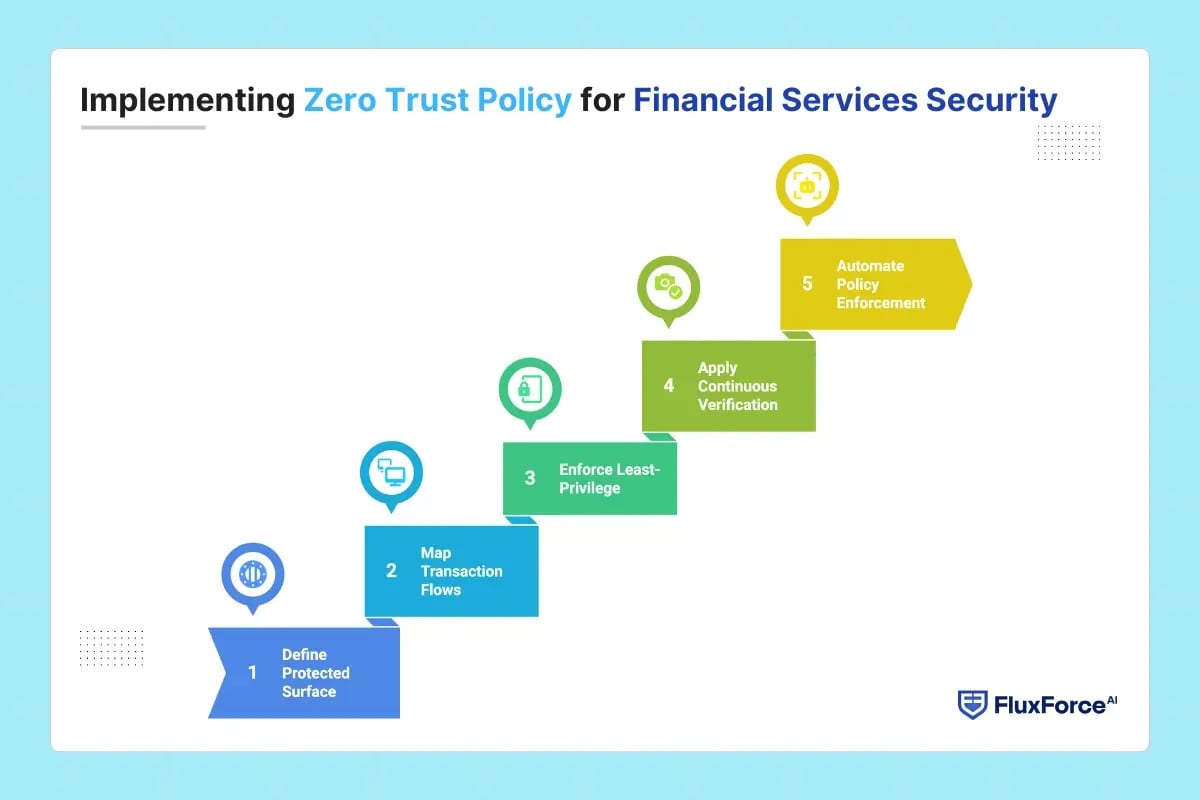
Zero Trust security architecture provides banking operational heads with a strategic framework to combat modern cyber threats. Here are the key steps that show how banks can implement a Zero Trust policy effectively:
Step 1: Define the Protected Surface
Banks must identify the most critical data, applications, and services (whether its customer data, mobile banking app, or loan services). By focusing on the protected surface, institutions can enforce strong controls where they matter most.
Step 2: Map Transaction Flows
Trace how data moves across applications, networks, and endpoints. Identify where credentials or sessions could be hijacked. Mapping flows shows potential lateral movement and allows precise access controls before attackers exploit weaknesses.
Step 3: Enforce Least-Privilege Access
Assign users, contractors, and partners only the permissions they need. Over-permissioned accounts create risk. Limiting access prevents internal misuse, accidental exposure, and attacker escalation while keeping operations efficient.
Step 4: Apply Continuous Verification
Monitor all users, devices, and sessions continuously. Check device integrity, user behaviour, and access context in real time. This ensures trust is never assumed and stops attackers from moving freely with compromised credentials.
Step 5: Automate Policy Enforcement
Manual access management slows operations and introduces errors. Automation grants and revokes access, enforces adaptive rules, and keeps audit-ready logs. It closes gaps, reduces overhead, and supports regulatory compliance.
-1.png?width=1200&height=628&name=hubspot%20blog%20(6)-1.png)
Shaping the Future of AI in Finance
Fluxforce research uncovers how banks and enterprises are adapting to fraud, compliance, and data challenges in 2025.
Core Principles of Zero Trust Security in Banking Network Environments
The Zero Trust Security framework is established on key principles that guide secure access across banking systems. These principles are:
- Continuous Identity Verification for Secure Banking Access
Authenticate every user, device, and system. MFA, biometrics, and adaptive verification prevent unauthorized access and reduce insider threats across banking operations.
- Enforce Least Privilege Across Banking Systems
Grant users and systems only required permissions. Role- and attribute-based controls limit unauthorized transactions and protect sensitive financial data.
- Micro-Segmentation to Protect Critical Banking Assets
Segment core banking systems to restrict lateral movement. Contain breaches and safeguard customer accounts, payment platforms, and transaction-critical data.
- Real-Time Monitoring and Risk Analytics
Continuously monitor network activity and user behaviour. AI-driven analytics detect anomalies, enabling proactive threat response and fraud mitigation.
- Endpoint Security and Compliance Enforcement
Verify all connecting devices. Endpoint detection, encryption, and patch management prevent compromised devices from introducing operational and security risks.
- Data Protection Across All States
Encrypt data at rest, in transit, and in use. Logging and monitoring prevent exfiltration and ensure regulatory compliance.
- Assume Breach and Maintain Incident Preparedness
Operate under “never trust, always verify.” Continuous audits, incident response, and automated containment prepare banks for potential breaches.
- Automated Threat Response for Operational Continuity
Automate threat detection and remediation. Suspicious activity triggers immediate action, reducing operational, financial, and reputational impact.
Proven Zero Trust Access Control Strategies for Banking Operations Heads
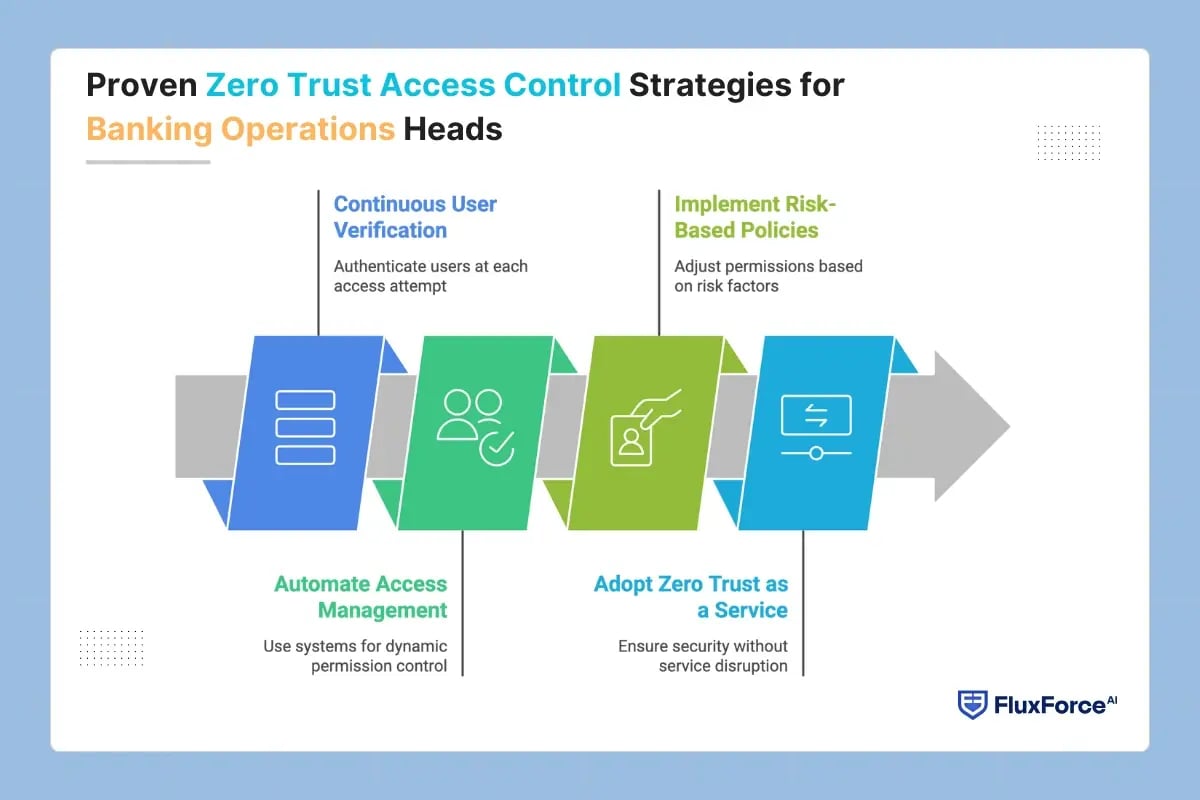
Zero Trust policies deliver maximum security when banks align structured best practices with advanced technology solutions. Key strategies include:
1. Continuous User Verification to Prevent Insider ThreatsInsider threats account for nearly 30% of data breaches in financial institutions. Zero Trust ensures that a user authenticated and authorized every time before accessing sensitive systems. It helps banks reduce the likelihood of insider data leaks and unauthorized access.
2. Automate Access Management for Efficiency and SecurityManual access reviews are time-consuming and error prone. Operations heads should deploy automated access control systems that grant and revoke permissions dynamically.
3. Implement Risk-Based Adaptive Access PoliciesBanking fraud detection requires proactive measures. Banks should adopt adaptive AI-enabled access models that adjust permissions based on user behaviour, device health, and location. This strategy minimizes fraudulent transactions while enabling legitimate users to operate smoothly.
4. Adopt Zero Trust as a Service for Disruption-Free BankingFinancial institutions often face challenges in maintaining uninterrupted services while upgrading security. Leveraging Zero Trust as a Service allows banks to implement robust security frameworks without affecting customer operations. This approach ensures continuous protection with minimal operational downtime.
Compliance and Customer Trust Benefits of Zero Trust Security
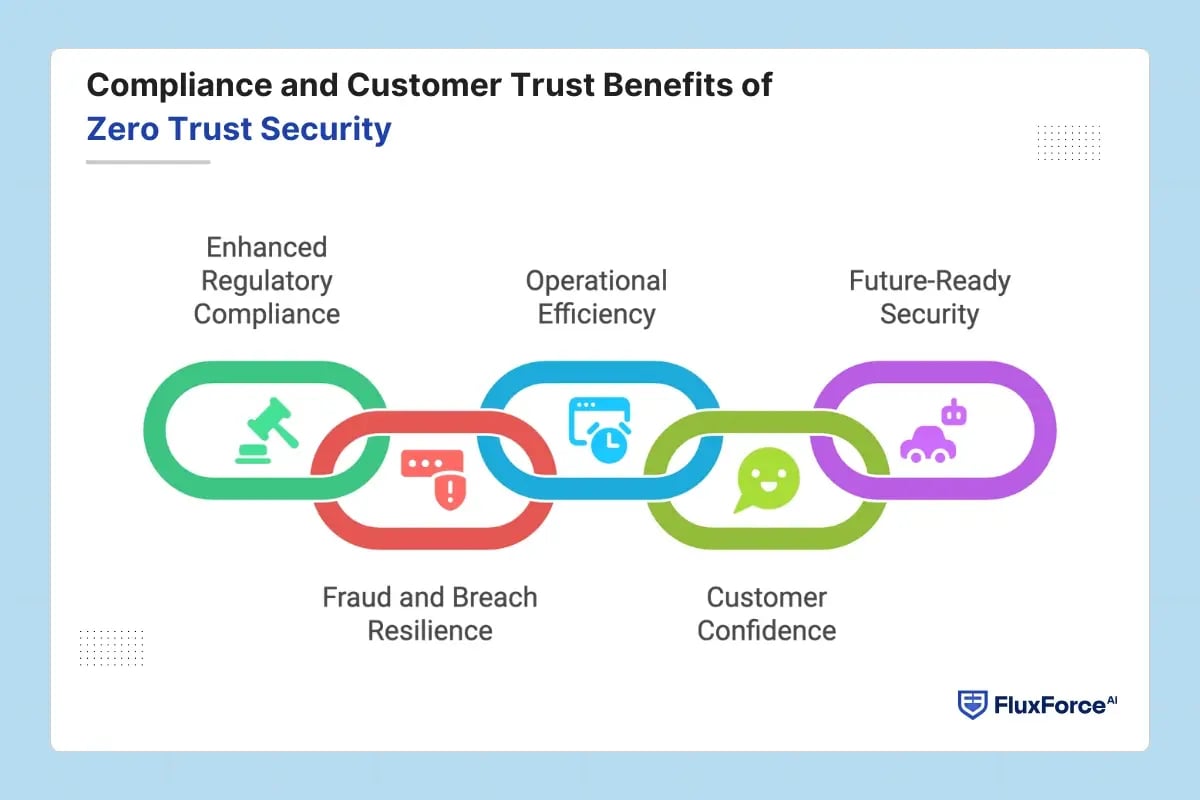
Implementing Zero Trust strengthens both regulatory compliance and customer confidence. Key benefits include:
Enhanced Regulatory Compliance – Real-time logs, audit trails, and automated enforcement simplify adherence to PCI DSS, GDPR, CCPA, and central bank requirements, reducing non-compliance risks.
Fraud and Breach Resilience – Continuous verification, micro-segmentation, and risk-based access policies limit lateral movement, preventing unauthorized access and insider or external threats.
Operational Efficiency – Automation enforces consistent access policies, reduces manual oversight, and secures cloud, API, and on-premises banking environments efficiently.
Customer Confidence – Proactive access controls reassure clients that accounts, transactions, and sensitive information are protected against breaches, fraud, and insider misuse.
Future-Ready Security – Zero Trust frameworks adapt to emerging technologies, cloud adoption, and evolving threat landscapes, ensuring long-term protection and supporting banking digital transformation.
Conclusion
Security in financial services must be robust and resilient, addressing evolving threats while maintaining operational continuity. Zero Trust Architecture provides banking operational heads with a framework to enforce strict access controls, verify identities continuously, and monitor systems in real time.
By embedding automation and real-time monitoring, banks can respond to threats proactively, maintain regulatory compliance, and safeguard sensitive customer data without disrupting operations.
Zero Trust ensures operational resilience while enabling seamless workflows across cloud, API, and on-premises systems.
For banks, ensuring disruption-free operations is always a challenge, yet Zero Trust as a Service allows institutions to strengthen access controls, reduce risk, and maintain customer trust.


.webp)
.webp)


Share this article