Listen to Our Podcast🎧

Introduction
Chief Information Security Officers are not only responsible for network safety anymore. They also need to manage high-risk supplier validation and third-party risk management as part of overall supply chain security. If supplier checks are weak, it can lead to fraud, fines, and supply chain breakdowns.
The data confirms this risk. PwC’s Global Economic Crime and Fraud Survey 2022 showed that 52% of companies faced fraud through third parties or suppliers. That makes AML compliance and identity verification key requirements, not just a matter of paperwork.
For CISOs, supplier due diligence is now part of core security work. Vendors marked as high-risk suppliers often deal with high-risk products, operate in regions with poor oversight, or hide who really owns them. Without strong identity verification and AML checks, these vendors can create serious gaps in compliance and business operations.
As Satya Nadella said,
“Finally, trust is the foundation upon which everything we do is built. That’s why we’ve invested heavily in security and compliance that set the standard for enterprises.”
For CISOs, trust in supply chains begins with KYC for suppliers. Companies that apply the right supplier due diligence process can build stronger and safer supply chains where every vendor is checked, monitored, and trusted.
KYC and AML Compliance in Supplier Due Diligence
When CISOs oversee supplier due diligence, two pillars hold the process together: Know Your Customer (KYC) and Anti-Money Laundering (AML) compliance. These are no longer just financial-sector rules. They are now applied to supplier onboarding and third-party risk management across global supply chains.
KYC checks help companies confirm the true identity of their vendors. By using identity verification tools and reviewing ownership records, businesses reduce the chance of onboarding high-risk suppliers hiding behind shell structures.
AML controls add another layer. Screening suppliers against sanctions lists and monitoring for unusual financial behavior lowers exposure to fraud and reputational damage. A recent World Bank report highlighted that money laundering and related crimes cost the global economy between 2–5% of GDP annually, proving why AML controls are now embedded in procurement practices.
Together, KYC and AML compliance form the base of a strong supplier due diligence process. They give CISOs the data needed to make informed calls about which vendors are safe to onboard and which qualify as high-risk vendors requiring deeper checks.
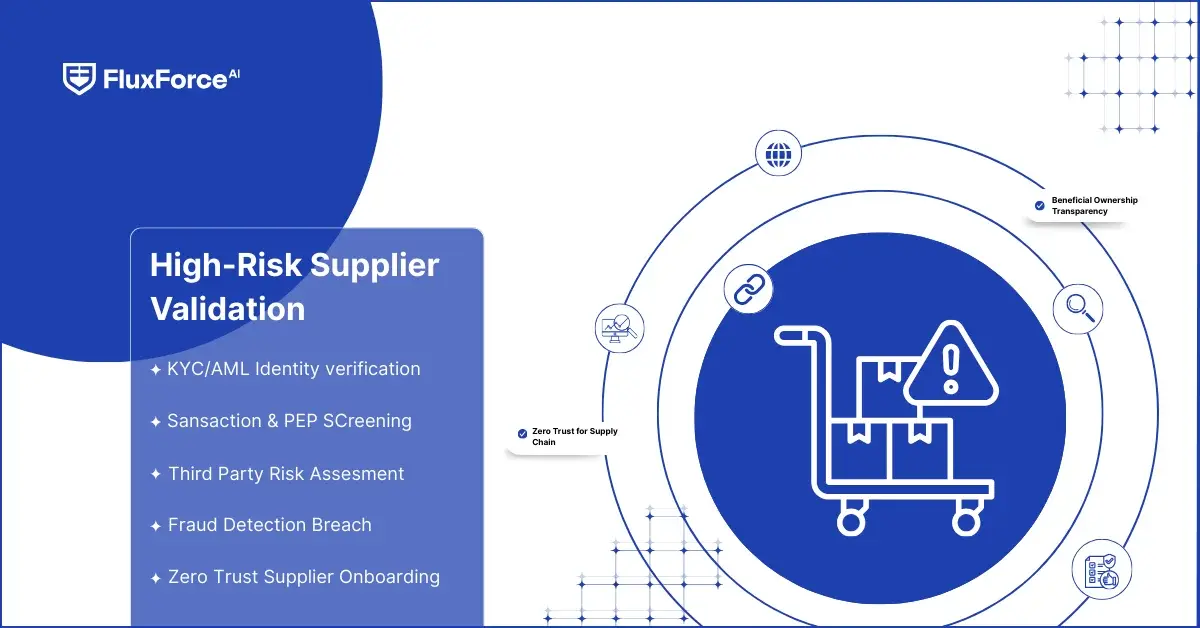
Identity Verification Strategies for High-Risk Vendors

Strengthening Identity Verification
For high-risk suppliers, checking basic documents is not enough. CISOs need identity verification strategies that use digital onboarding, biometric checks, and ownership records. This helps reveal hidden owners and stops risk vendors from slipping through using shell companies.
Using Technology for Ongoing Checks
Modern identity verification tools work with compliance automation solutions to run real-time checks on suppliers. They compare vendor data with sanctions lists and regulatory watchlists. These ongoing checks reduce the chance of relying on outdated or false supplier information.
Connecting Verification to Supplier Risk
Identity checks should tie into third-party risk management. High-risk vendors should be monitored against key risk indicators for vendor management. This gives CISOs clear visibility and allows fast action if a supplier’s risk level changes.
Onboard Customers in Seconds
Vendor Risk Management Best Practices for CISOs

Building a Practical Vendor Risk Management Plan
Managing high-risk vendors requires clear vendor risk management best practices. CISOs should classify suppliers by risk level using supplier risk information, past performance, and key risk indicators for vendor management. High-risk suppliers should get enhanced due diligence and continuous monitoring.
Monitoring Supplier Security and Compliance
Regular checks on vendor security risk and vendor cybersecurity help prevent breaches through third parties. Integrating vendor security management tools with the supplier due diligence process ensures that any change in vendor behavior or compliance status triggers alerts for immediate action.
Mitigation and Offboarding
CISOs must have a clear vendor risk mitigation plan and define processes for vendor offboarding when risk levels become unacceptable. Removing high-risk suppliers promptly protects supply chain security and maintains regulatory compliance.

Shaping the Future of AI in Finance
Fluxforce research uncovers how banks and enterprises are adapting to fraud, compliance, and data challenges in 2025.
CISO Strategies for Continuous Supplier Monitoring and Risk Reduction

Continuous Supplier Monitoring
CISOs should use continuous supplier monitoring to keep an eye on high-risk vendors at all times. Automated systems track changes in supplier ownership, compliance status, and operational behavior. This provides up-to-date supplier risk information that helps security teams take action quickly. Ongoing monitoring also supports third-party risk management and reduces the chance of unexpected supply chain disruptions.
Vendor Risk Mitigation and Offboarding
A clear vendor risk mitigation plan is essential. CISOs should define what level of risk is acceptable for each supplier. If a supplier exceeds this level, vendor offboarding must be carried out without delay. Removing high-risk vendors protects supply chain security, ensures AML compliance, and lowers the risk of fraud or regulatory fines.
Integrating Security Across the Supplier Lifecycle
Security should be built into every step of the supplier due diligence process. Using identity verification tools and compliance automation solutions during onboarding, monitoring, and offboarding helps maintain vendor cybersecurity and vendor security management. This ensures that all suppliers are verified, risks are minimized, and the supply chain stays secure and compliant.
Conclusion
From digital onboarding to compliance automation, technology now makes it possible to detect risks before they become major incidents. By applying advanced identity verification tools and continuous monitoring, CISOs can transform supplier risk management into a proactive, automated shield for the organization.





Share this article